Service Keys¶
The key value store of Consul administrates the Output Engine server configuration.
You can change the key via the Consul Web interface (see Consul) or via PLOSSYS CLI (see Administrate the System Configuration).
Units¶
Size¶
Values with size specifications are specified in the following size units:
-
bytes(B) -
kilobytes(KB) -
megabytes(MB) -
gigabytes(GB)
Example - with size units
10 Megabytes: 10MB
Time¶
Values with time specifications are specified in the following time units:
-
seconds(s,sec) -
minutes(m,min) -
hours(h,hr) -
days(d) -
weeks(w,wk) -
months -
years(y,yr)
Example - with time units
2 hours and 30 minutes: 2h30m
4 minutes and 2 seconds: 4m2s
ACCOUNTING¶
ACCOUNTING specifies customer-specific accounting items in JSON format. The JSON key is identical to the key of the accounting item, the value is the reference to the job or printer item logged as value of the accounting item, refer to the example below.
The following job items are added by the seal-plossys-accounting service:
job.completed.dateDate part of the completed time as human-readable string (YYYY-MM-DD)job.completed.timeTime part of the completed time as human-readable string (hh-mm-ss)job.completed.totalProcessing duration in secondsjob.checkin.dateDate part of the checkin time as human-readable string (YYYY-MM-DD)job.checkin.timeTime part of the checkin time as human-readable string (hh-mm-ss)job.origPrinterNameOriginal printer namejob.hostnameServer name
The key is available for the seal-plossys-accounting service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossys-accounting/tag/any/ACCOUNTING
Available values: JSON string format
Default: none
Example - customized accounting configuration in Consul
{
"printerModel": "printer.type.model",
"printerBrand": "printer.type.manufacturer",
"server": "job.hostname",
"completedDate": "job.completed.date",
"completedTime": "job.completed.time",
"totaltimeTaken": "job.completed.total",
"fix": "'LITERAL STRING'"
}
ALLOWED_OIDC_CLIENTS¶
ALLOWED_OIDC_CLIENTS specifies the mapping of permissions to roles specified in the OIDC identity provider. For more information, refer to Permissions and OIDC Roles for Linux or Permissions and OIDC Roles for Windows.
The key is available for the seal-rest service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/rest/tag/any/ALLOWED_OIDC_CLIENTS
Available values: JSON string format
Default: none
Hint - create template
The value of ALLOWED_OIDC_CLIENTS has to accord to a specific JSON object. With PLOSSYS CLI, a template can be generated which then only has to be filled out. The example below creates the template and saves it as template.json in the current directory.
plossys config template ALLOWED_OIDC_CLIENTS --file template.json
AUDIT_LOG¶
AUDIT_LOG specifies if audit data is logged.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/AUDIT_LOG
Available values: String
-
YAudit data is logged.
-
NAudit data is not logged.
Default: Y
AUDIT_LOG_USER¶
AUDIT_LOG_USER specifies if the user names are logged in the audit data.
The key is available for the seal-rest service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/rest/tag/any/AUDIT_LOG_USER
Available values: String
-
YThe user names are logged in the audit data.
-
NThe user names are not logged in the audit data.
Default: N
AUTH_ADDITIONAL_SCOPES¶
AUTH_ADDITIONAL_SCOPES specifies additional scopes for OAuth 2 (required for Azure AD for example). Multiple scopes are separated by a blank.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/AUTH_ADDITIONAL_SCOPES
Available values: String
<scope_1> <scope_2> ... <scope_n>
Default: none
AUTH_CLIENT_ID¶
AUTH_CLIENT_ID specifies the client name configured in the OIDC identity provider for retrieving the access token.
The key is available for the following services:
-
seal-plossysadmin -
seal-plossyscli
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/plossysadmin/tag/any/AUTH_CLIENT_ID -
dc/home/env/service/plossyscli/tag/any/AUTH_CLIENT_ID
Available values: String
<client_id>
Default:
-
seal-plossyscliservice:seal-plossyscli -
seal-plossysadminservice:seal-plossysadmin
AUTH_CLIENT_SECRET¶
AUTH_CLIENT_SECRET specifies the client secret for retrieving the OIDC identity provider's access token.
The key is available for the following services:
-
seal-plossysadmin -
seal-plossyscli
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/plossysadmin/tag/any/AUTH_CLIENT_SECRET -
dc/home/env/service/plossyscli/tag/any/AUTH_CLIENT_SECRET
Available values: String
<client_secret>
Default: not revealed
AUTH_CLOCK_TOLERANCE¶
AUTH_CLOCK_TOLERANCE specifies the number of seconds allowed as time difference between the OIDC identity provider and the client.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/AUTH_CLOCK_TOLERANCE
Available values: String
<number_seconds>
Default: 5
AUTH_DEFAULT_SESSION_DURATION¶
AUTH_DEFAULT_SESSION_DURATION specifies the duration of the default session in seconds if the OIDC identity provider does not expose the refresh_expires_in parameter in the token.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/AUTH_DEFAULT_SESSION_DURATION
Avaialble values: String
<number_sessions>
Default: 180
AUTH_IDP_CONNECT_TIMEOUT¶
AUTH_IDP_CONNECT_TIMEOUT specifies the timeout for the connection to the OIDC identity provider. The time has to be specified in seconds.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/AUTH_IDP_CONNECT_TIMEOUT
Avaialble values: String
<number_seconds>
Default: 60
AUTH_IDP_REQUEST_TIMEOUT¶
AUTH_IDP_REQUEST_TIMEOUT specifies the timeout for authentication requests to the OIDC identity provider. The time has to be specified in seconds.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/AUTH_IDP_REQUEST_TIMEOUT
Avaialble values: String
<number_seconds>
Default: 10
AUTH_ISSUER_URL¶
AUTH_ISSUER_URL specifies the OIDC issuer URL. This URL is configured in Keycloak for example. For more information about Keycloak used with SEAL Systems products, refer to the SEAL Interfaces for OIDC documentation.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/AUTH_ISSUER_URL
Available values: String
<oidc_issuer_url>
Default: https://localhost:32769/auth/realms/SEAL
Hint - changed AUTH_ISSUER_URL as of Keycloak 21.0.1
As of SEAL-specific Keycloak version 21.0.1, the URL needed for `AUTH_ISSUER_URL has been changed.
-
old value:
AUTH_ISSUER_URL=https://<hostname>:32769/auth/realms/SEAL -
new value:
AUTH_ISSUER_URL=https:/<hostname>:32769/realms/SEAL
AUTH_REDIRECT_PROTOCOL¶
AUTH_REDIRECT_PROTOCOL specifies the transfer protocol.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/AUTH_REDIRECT_PROTOCOL
Available values: String
-
http -
https
Default: The protocol of the user interface server is used.
AUTH_REFRESH_TOLERANCE¶
AUTH_REFRESH_TOLERANCE specifies the number of seconds after which a token will be refreshed when it is about to expire.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/AUTH_REFRESH_TOLERANCE
Available values: String
<number_seconds>
Default: 5
AUTH_TOKEN_TYPE¶
AUTH_TOKEN_TYPE specifies the type of the token used for the authentication against the REST API.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/AUTH_TOKEN_TYPE
Available values: String
-
access_tokenThe access token is used.
-
id_tokenThe ID token is used.
Default: access_token
AUTH_TYPE¶
AUTH_TYPE specifies the mode of the client authentication.
The key is available for the following services:
-
seal-ipp-checkin -
seal-job-notifier -
seal-rest -
seal-mainland-checkout
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/checkin/tag/ipp/AUTH_TYPE -
dc/home/env/service/job-notifier/tag/any/AUTH_TYPE -
dc/home/env/service/rest/tag/any/AUTH_TYPE -
dc/home/env/service/mainland-checkout/tag/any/AUTH_TYPE
Available values: String
-
apiKeyAPI keys are needed for the authentication (only
seal-mainland-checkoutservice). -
basicThe service accepts any authentication. This is implemented by the
Basic Authauthentication. -
certClient certificates are needed for the authentication (only
seal-mainland-checkoutservice). -
oidcIn the request the service expects a JSON Web token (JWT) which is received from an authentication via OpenID server connect (not
seal-mainland-checkoutservice). -
oidc basicUse
oidcandbasicconcurrently (onlyseal-restservice).
Default:
-
apiKey(seal-mainland-checkout) -
oidc(all other services)
Hint - in practice
In practice, for seal-rest service only oidc is relevant due to PLOSSYS Administrator only working with oidc and using multiple user authentications does not make sense.
AVAILABLE_LANGUAGES¶
AVAILABLE_LANGUAGES specifies the languages provided to the user in the user interface, PLOSSYS Adminstrator. With the same name, a language file (<language>.json) has to exist in C:\Program Files\SEAL Systems\seal-plossysadmin\public\assets\i18n on Windows or /opt/seal/seal-plossysadmin/public/assets/i18n on Linux. Multiple languages are separated by comma.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/AVAILABLE_LANGUAGES
Available values: String
<language1>,<language2> ... <languagex>
Default: de,en
BROKER_FORCE_TLS¶
BROKER_FORCE_TLS specifies if the SEAL NATS message broker uses TLS.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/BROKER_FORCE_TLS
Available values: Boolean
false-
N -
true Y
Default: false
BROKER_PUBLISH_RETRY¶
BROKER_PUBLISH_RETRY specifies the number of retries to publish a message to the NATS message broker if it failed at first try.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/BROKER_PUBLISH_RETRYdc/home/env/service/checkin/tag/ipp/BROKER_PUBLISH_RETRY
Available values: Number
Default:
1(one) retry for seal-ipp-checkin10(ten) retries for all other services
BROKER_SERVERS¶
BROKER_SERVERS specifies the message broker server hosts and ports. Multiple server and port items are separated by commas.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/BROKER_SERVERS
Available values: String
nats1:4222,nats2:4222,nats3:4222
Default: localhost:4222
BROKER_REJECT_UNAUTHORIZED¶
BROKER_REJECT_UNAUTHORIZED specifies if self-signed TLS certificates from the message broker will be rejected. Only used if BROKER_FORCE_TLS is enabled.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/BROKER_REJECT_UNAUTHORIZED
Available values: Boolean
true-
Y -
false N
Default: true
BROKER_TOKEN¶
BROKER_TOKEN specifies the message broker access token.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/BROKER_TOKEN
Available values: String
Default: none
CACERT¶
CACERT specifies the certificate of the certification authority (CA) that issued the client certificates, if AUTH_TYPE is set to cert.
The key is available for the seal-mainland-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/anymainland-checkout/tag/any/CA_CERT
Available values: String (file to be read or content)
Default: none
CALLBACK_NOTIFICATIONS_INTERVAL¶
CALLBACK_NOTIFICATIONS_INTERVAL specifies the time after which the seal-co-notifier service will send previously failed callback notifications again. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-co-notifier service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/co-notifier/tag/any/CALLBACK_NOTIFICATIONS_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 10s
CATCH_ALL_PRINTER¶
CATCH_ALL_PRINTER specifies the name of the printer which should receive print jobs for unknown printers. Jobs for a printer that does not exist in the database are treated as erroneous by default. If a printer has been specified with CATCH_ALL_PRINTER, these jobs are redirected to the specified printer instead.
The key is available for the following services:
-
seal-checkin -
seal-ipp-checkin
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/checkin/tag/lpr/CATCH_ALL_PRINTER -
dc/home/env/service/checkin/tag/ipp/CATCH_ALL_PRINTER
Available values: String
<printer_name>
Default: none
CHECK_TIMEOUT¶
CHECK_TIMEOUT specifies the timeout in milliseconds after which a connection check is automatically aborted.
The key is available for the following services:
seal-rest
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/rest/tag/any/CHECK_TIMEOUT
Available values: Integer
<timeout_in_milliseconds>
Default: 5000
CHECKIN_TIME_FROM_DB¶
CHECKIN_TIME_FROM_DB specifies whether the checkin services or the database sets the checkin time of the new output jobs. Setting by the checkin services is faster and consumes less resources. However, the database can guarantee a correct checkin time if keeping the times synchronous on all servers belonging to the cluster is impossible.
Caution - MongoDB version
Only MongoDB as of version 4.2 supports this feature!
The key is available for the following services:
-
seal-checkin -
seal-ipp-checkin
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/checkin/tag/lpr/CHECKIN_TIME_FROM_DB -
dc/home/env/service/checkin/tag/ipp/CHECKIN_TIME_FROM_DB
Available values: Boolean
-
trueThe database sets the checkin time.
-
falseThe checkin service sets the checkin time.
Default: false
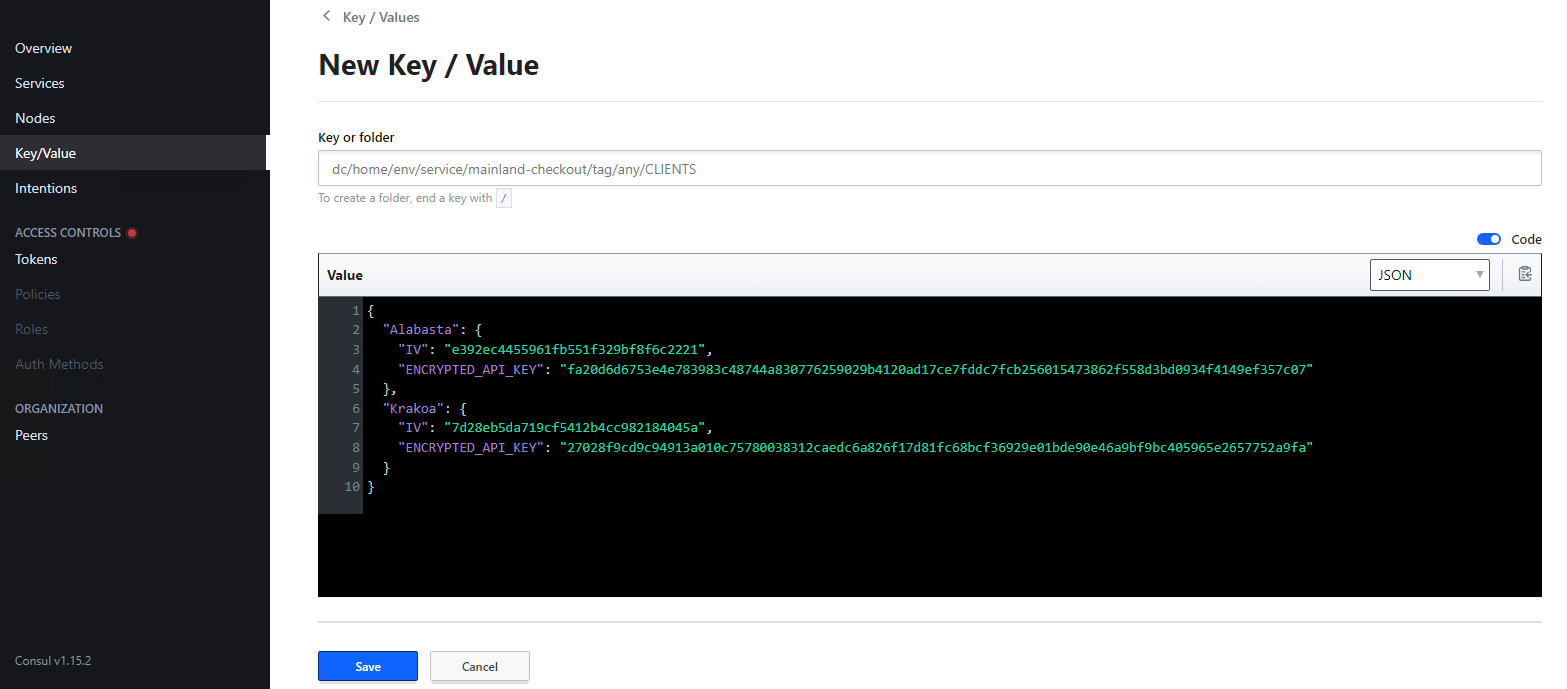
CLIENTS¶
CLIENTS specifies remote sites and their API Keys. The name specified for each remote site has to be the one used to create the API keys and to configure the respective queues in easyPRIMA. The key is only evaluated if AUTH_TYPE for seal-mainland-checkout service is set to apiKey.
The key is available for the seal-mainland-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/mainland-checkout/tag/any/CLIENTS
Available values: JSON string format
Default: none
Example
When generating custom API keys for remote sites, the result will contain two sets of secrets per island: one for the island and one for the mainland. The keys needed for seal-mainland-checkout are highlighted. On how to create API keys via PLOSSYS CLI, refer to API Key Creation.
{
"Alabasta": {
"DECRYPTION_SECRET": "09d63b8576ae85c0865d99c6386078691b8634ae825e1026f622a1d54b07263b",
"IV": "dfbadfa64a02cc7e05f87e75f836006e",
"API_KEY": "2098c2b400e2b0152e6f904d0fb75d9ab8da655a27a0da0f1d96b4c5ebe01c9b",
"ENCRYPTED_API_KEY": "7f4d47950b1d5c66168f5e6c667479298c45a03c6637a5b9f48dfe6df669fa3b9d1eb1312691b8a0801ceca556d884af"
},
"mainland": {
"DECRYPTION_SECRET": "6edb0f5038052bf1de7194d5cf82c89eebdf490b61405838eb1e1bb19915c6e4",
"IV": "e392ec4455961fb551f329bf8f6c2221",
"API_KEY": "2098c2b400e2b0152e6f904d0fb75d9ab8da655a27a0da0f1d96b4c5ebe01c9b",
"ENCRYPTED_API_KEY": "fa20d6d6753e4e783983c48744a830776259029b4120ad17ce7fddc7fcb256015473862f558d3bd0934f4149ef357c07"
}
}
The mainland ENCRYPTED_API_KEY and IV are the ones used for CLIENTS. They are unique for each remote site.
CONFIG¶
CONFIG specifies the customized content of the CONFIG configuration file required by the SAPGOF converter.
Literature - SAPGOF Converter
For further information about how to configure the SAPGOF Converter, refer to the SAPGOF Converter documentation.
The key is available for the SAPGOF converter.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/plossys/convert-sapgof/CONFIG
Available values: String
<content_config_file>
Default: none (The settings in C:\Program Files\SEAL Systems\seal-convert-sapgof\lib\initialization\config\CONFIG are used.)
CONFIG_DIR¶
CONFIG_DIR specifies the name of the directory which contains the configuration of the services unless the configuration is read from Consul.
The key is available for the following services:
-
seal-convert-pdfstamp -
seal-convert-sapgof
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/<service>/any/tag/any/CONFIG_DIR
Available values: String
<config_dir>
Default: none (The settings are read from Consul.)
CONSUL_DOMAIN¶
CONSUL_DOMAIN specifies the domain with which the Output Engine services log on.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/CONSUL_DOMAIN
Available values: String
<domain_name>
Default: consul
CONSUL_FORCE_TLS¶
CONSUL_FORCE_TLS specifies if the consul uses TLS.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/CONSUL_FORCE_TLS
Available values: Boolean
false-
N -
true Y
Default: Depends on the value of TLS_UNPROTECTED
CONSUL_TOKEN¶
CONSUL_TOKEN specifies the ACL token with which the Output Engine services authenticate themselves to Consul.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/CONSUL_TOKEN
Available values: String
<token>
Default: INSECURE_ACL_MASTER_TOKEN
CONSUL_URL¶
CONSUL_URL specifies the URL of the Consul server to which the Output Engine services log on.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/CONSUL_URL
Available values: String
<consul_url>
Default: https://localhost:8500
CONVERT_ON_PRINTER_START¶
CONVERT_ON_PRINTER_START specifies if waiting jobs are scheduled for conversion on printer start.
The key is available for the following services:
-
seal-rest(only for PLOSSYS 5.3.0 and usingseal-dispatcher) -
seal-controller
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/rest/tag/any/CONVERT_ON_PRINTER_START(only for PLOSSYS 5.3.0 and usingseal-dispatcher) -
dc/home/env/service/controller/tag/any/CONVERT_ON_PRINTER_START
Available values: String
-
YWhen a printer starts, waiting jobs for this printer are scheduled for conversion.
-
NWhen a printer starts, waiting jobs for this printer are not scheduled for conversion.
Default: N
CONVEYOR_LOG_CONNECT¶
CONVEYOR_LOG_CONNECT enables additional log messages concerning the streaming of job data in PLOSSYS Output Engine.
The key is available for the following services:
seal-bodyscannerseal-ghostseal-copierseal-checkoutseal-pjl-ceckout
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/bodyscanner/tag/any/CONVEYOR_LOG_CONNECTdc/home/env/service/ghost/tag/any/CONVEYOR_LOG_CONNECTdc/home/env/service/copier/tag/any/CONVEYOR_LOG_CONNECTdc/home/env/service/checkout/tag/any/CONVEYOR_LOG_CONNECTdc/home/env/service/pjl-checkout/tag/any/CONVEYOR_LOG_CONNECT
Instead of setting the key for each service, it can also be specified here once and for all:
dc/home/env/service/any/tag/any/CONVEYOR_LOG_CONNECT
Available values: Boolean
false-
N -
true Y
Default: false
CUSTOM_FLOW_<environment_variable>¶
CUSTOM_FLOW_<environment_variable> specifies the value for the environment variable <environment_variable> which is passed to the main flow processed by the seal-convert-dispatcher service.
The key is available for the seal-convert-dispatcher service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/convert-dispatcher/tag/any/CUSTOM_FLOW_<environment_variable>
Available values: String
<value>
Default: none
Example - pass COLOR set to blue
When dc/home/env/service/convert-dispatcher/tag/any/CUSTOM_FLOW_COLOR has been set to blue in Consul, the seal-convert-dispatcher service passes the COLOR environment variable with the value blue to the main flow.
DECRYPTION_SECRET¶
DECRYPTION_SECRET specifies the general decryption secret used to decrypt the API Keys for the remote sites, if AUTH_TYPE for the seal-mainland-checkout service is set to apiKey.
The key is available for the seal-mainland-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/mainland-checkout/tag/any/DECRYPTION_SECRET
Available values: string
Default: none
Literature - Remote Printing
Refer to Configure Remote Printing Using API Keys.
DEFAULT_AUTO_RELOAD_INTERVAL¶
DEFAULT_AUTO_RELOAD_INTERVAL specifies the default polling interval in seconds to auto refresh the jobs and printers tables in PLOSSYS Administrator.
The key is available for the seal-plossysadmin service:
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/DEFAULT_AUTO_RELOAD_INTERVAL
Available values: Number
-
Range is between 1 - 60.
Values bigger than 60 will be treated as 60. Values smaller than 1 will be treated as 1.
Default: 5
DEFAULT_COLOR_MODEL¶
DEFAULT_COLOR_MODEL specifies the default color used for accounting if no color model is set in printed document.
The key is available for the seal-plossys-accounting service:
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossys-accounting/tag/any/DEFAULT_COLOR_MODEL
Available values: String
-
colorUse
coloras color model for all pages with unkown color model. -
grayUse
grayas color model for all pages with unkown color model.
Default: color
DOCUMENT_STREAM_TIMEOUT¶
DOCUMENT_STREAM_TIMEOUT specifies the inactivity timeout of a printer after processing the last job of a document stream. The time has to be specified including the unit. For the available units, refer to Units at the top of the page. For information about document streams, refer to Document Streams.
The key is available for the following services:
seal-controller
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/controller/tag/any/DOCUMENT_STREAM_TIMEOUT
Available values: Integer
<timeout_in_milliseconds>
Default: 1m
ELASTICSEARCH_INDEX_LOG¶
ELASTICSEARCH_INDEX_LOG specifies the index where the log data is stored in Elasticsearch.
The key is available for the following service:
seal-rest
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/rest/tag/any/ELASTICSEARCH_INDEX_LOG
Available values: String
<index_name>
Default: seal-plossys-5-log
ELASTICSEARCH_INDEX_STATISTICS¶
ELASTICSEARCH_INDEX_STATISTICS specifies the index with which the statistics data is stored in Elasticsearch.
The key is available for the seal-rest service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/rest/tag/any/ELASTICSEARCH_INDEX_STATISTICS
Available values: String
<index_name>
Default: seal-plossys-5-statistics
ELASTICSEARCH_REST_URL¶
ELASTICSEARCH_REST_URL specifies the URL of the Elasticsearch server.
The key is available for the seal-rest service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/rest/tag/any/ELASTICSEARCH_REST_URL
Available values: String
<elasticsearch_url>
Default: http://localhost:9200
FEAT_LOG_NATSINFO¶
FEAT_LOG_NATSINFO enables additional log messages concerning the initialization of the NATS message broker.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/FEAT_LOG_NATSINFO
Available values: Boolean
true-
YEnables additional log messages
-
false -
NDisables additional log messages
Default: false
GRIBS74_PDF_DB¶
GRIBS74_PDF_DB contains the customized content of the GRIBS74_PDF_DB configuration file required by the SAPGOF converter.
Literature - SAPGOF Converter
For further information about how to configure the SAPGOF Converter, refer to the SAPGOF Converter documentation.
The key is available for the SAPGOF converter.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/plossys/convert-sapgof/GRIBS74_PDF_DB
Available values: String
<content_gribs74_pdf_db_file>
Default: none (The settings in C:\Program Files\SEAL Systems\seal-convert-sapgof\lib\initialization\config\GRIBS74_PDF_DB are used.)
HOUSEKEEPER_ELECTION_TIMEOUT¶
HOUSEKEEPER_ELECTION_TIMEOUT specifies the time for the election between the seal-houskeeper service instances. One of those instances will win the election, and executes its tasks. The other ones do nothing. The election is repeated on every HOUSEKEEPER_INTERVAL. It is recommended with the cluster mode for reducing the load on MongoDB. The value should be less than the value specified with HOUSEKEEPER_INTERVAL, but more than 10s. The time has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/HOUSEKEEPER_ELECTION_TIMEOUT
Available values: String
-
<time_interval_and_unit> -
-1The election will be skipped. Each
seal-housekeeperservice instance executes all preconfigured tasks.
Default: -1
HOUSEKEEPER_INTERVAL¶
HOUSEKEEPER_INTERVAL specifies the time interval after which the seal-housekeeper service searches for jobs to delete. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/HOUSEKEEPER_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 1h
HTPASSWD¶
HTPASSWD specifies the valid users when basic authentication is used. The value has to accord to the format used in the Apache htpasswd file, which is user:password. If HTPASSWD is set, HTPASSWD_FILE will be ignored.
The key is available for the following services:
-
seal-rest -
seal-job-notifier -
seal-mainland-checkout
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/rest/tag/any/HTPASSWD -
dc/home/env/service/job-notifier/tag/any/HTPASSWD
Available values: String
<htpasswd_content>
Default: none
HTPASSWD_FILE¶
HTPASSWD_FILE specifies the location of the password file which contains the valid users when basic authentication is used. The content of this file has to accord to the format of the Apache htpasswd file.
The key is available for the following services:
-
seal-housekeeper -
seal-ipp-checkin -
seal-rest -
seal-mainland-checkout
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/housekeeper/tag/any/HTPASSWD_FILE -
dc/home/env/service/checkin/tag/ipp/HTPASSWD_FILE -
dc/home/env/service/rest/tag/any/HTPASSWD_FILE
Available values: String
<htpasswd_path>
Default: none
ID_PROVIDER_CERT¶
ID_PROVIDER_CERT specifies the path and the file name of the certificate generated by the OIDC identity provider.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/ID_PROVIDER_CERT
Available values: String
<path_name>
Default: none
ID_PROVIDER_NAME¶
ID_PROVIDER_NAME specifies the name of the OIDC identity provider. When using more than one OIDC identity provider, separate their names by blanks.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/ID_PROVIDER_NAME
The key is mandatory.
Available values: String
-
<id_provider_name>(For example, with Keycloak, it is a complete URL:https://<hostname>:32769/realms/SEAL) -
<id_provider_name_1> <id_provider_name_2>(For example, with Keycloak, they are complete URLs:https://<cluster internal hostname>:32769/realms/SEAL https://<cluster external hostname>:32769/realms/SEAL)
Default: none
Hint - changed ID_PROVIDER_NAME as of Keycloak 21.0.1
As of SEAL-specific Keycloak version 21.0.1, the URL needed for ID_PROVIDER_NAME has been changed.
-
old value:
ID_PROVIDER_NAME=https://<hostname>:32769/auth/realms/SEAL -
new value:
ID_PROVIDER_NAME=https://<hostname>:32769/realms/SEAL
IPP_JOBNOTIFY_WAITTIME¶
IPP_JOBNOTIFY_WAITTIME specifies the time after which the final status notification is replied to a source IPP system. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/IPP_JOBNOTIFY_WAITTIME
Available values: String
<time_interval_and_unit>
Default: 15m
IPP_NOTIFICATIONS_INTERVAL¶
IPP_NOTIFICATIONS_INTERVAL specifies the time after which the seal-co-notifier service will send previously failed notifications again. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-co-notifier service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/co-notifier/tag/any/IPP_NOTIFICATIONS_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 10s
IPP_SYSTEMS¶
IPP_SYSTEMS specifies the authentication and proxy configuration for the source IPP systems. The information is formatted as YAML.
The key is available for the seal-co-notifier service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/co-notifier/tag/any/IPP_SYSTEMS
Available values: String
<ipp_systems>
Default: none
Example - authentication configuration for the abcd:631 and xyz:631 systems
# user, password and proxy for system abcd:631
- system: abcd:631
user: hugo
password: hugopass
proxy: http://proxy:3128
# user and password for system xyz:631, proxy is not required
- system: xyz:631
user: egon
password: egonpass
ISLAND_PORT¶
ISLAND_PORT specifies the port used by the island-checkouts to connect to.
The key is available for the seal-mainland-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/mainland-checkout/tag/any/ISLAND_PORT
Available values: String
<portnumber>
Default: 2119
JOB_DISPATCHING (Deprecated with PLOSSYS 5.3.2)¶
JOB_DISPATCHING specifies the service used for dispatching the jobs.
Caution - deprecated
The seal-dispatcher service was used for dispatching the jobs up to PLOSSYS 5.3.0. The seal-controller service is available as of PLOSSYS 5.3.0. As of PLOSSYS 5.3.2, the seal-dispatcher service is no longer supported and the seal-controller service is always used. Therefore, the JOB_DISPATCHING key is deprecated.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/JOB_DISPATCHING
Available values: String
-
classicTheseal-dispatcherservice is used. -
nextTheseal-controllerservice is used.
Default: classic
JOB_LIFETIME_ACCOUNTING¶
JOB_LIFETIME_ACCOUNTING specifies the time interval after which a job with the Accounting status is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. The timeout is calculated from the moment the job gets the status Accounting.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_ACCOUNTING
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: -1
JOB_LIFETIME_CANCELED¶
JOB_LIFETIME_CANCELED specifies the time interval after which a job with the Canceled status is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. The timeout is calculated from the moment the job gets the status Canceled.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_CANCELED
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: 24h
JOB_LIFETIME_ERROR¶
JOB_LIFETIME_ERROR specifies the time interval after which a job with the Error status is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. The timeout is calculated from the moment the job gets the status Error.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_ERROR
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: 3d
JOB_LIFETIME_PAUSED¶
JOB_LIFETIME_PAUSED specifies the time interval after which a job with the Paused status is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. Base for the calculation of the timeout is the checkinTime of the job.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_PAUSED
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: 3d
JOB_LIFETIME_PREPROCESSING¶
JOB_LIFETIME_PREPROCESSING specifies the time interval after which a job with the Preprocessing status is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. Base for the calculation of the timeout is the checkinTime of the job.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_PREPROCESSING
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: -1
JOB_LIFETIME_PROCESSED¶
JOB_LIFETIME_PROCESSED specifies the time interval after which a job with the Processed status is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. The timeout is calculated from the moment the job gets the status Processed.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_PROCESSED
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: 1h
JOB_LIFETIME_PROCESSING¶
JOB_LIFETIME_PROCESSING specifies the time interval after which a job with the Processing status is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. Base for the calculation of the timeout is the checkinTime of the job.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_PROCESSING
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: -1
JOB_LIFETIME_PROCESSINGREMOTE¶
JOB_LIFETIME_PROCESSINGREMOTE specifies the time interval after which a job with the Processingremote status is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. Base for the calculation of the timeout is the checkinTime of the job.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_PROCESSINGREMOTE
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: -1
JOB_LIFETIME_WAITING¶
JOB_LIFETIME_WAITING specifies the time interval after which a job waiting in a non-pickup queue is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. Base for the calculation of the timeout is the checkinTime of the job.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_WAITING
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: -1
JOB_LIFETIME_WAITING_PICKUP¶
JOB_LIFETIME_WAITING_PICKUP specifies the time interval after which a job waiting in a pickup queue is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. Base for the calculation of the timeout is the checkinTime of the job.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_WAITING_PICKUP
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: 3d
JOB_LIFETIME_WAITPREPROCESSING¶
JOB_LIFETIME_WAITPREPROCESSING specifies the time interval after which a job waiting for preprocessing is deleted from the database by the seal-housekeeper service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL. Base for the calculation of the timeout is the checkinTime of the job.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/JOB_LIFETIME_WAITPREPROCESSING
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: -1
JOB_MAX_CONVERSION_COUNT¶
JOB_MAX_CONVERSION_COUNT specifies how often a job will be postponed by the seal-convert-dispatcher service in case a conversion fails. After exceeding the specified maximum of postponements, the job will be considered erroneous.
The key is available for the following services:
seal-convert-dispatcher
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/convert-dispatcher/tag/any/JOB_MAX_CONVERSION_COUNT
Available values: Integer
-
<number_max_conversion>The maximum number of times a job will be postponed.
Default: 10
JOB_MAX_POSTPONED_COUNT¶
JOB_MAX_POSTPONED_COUNT specifies how often a job will be postponed by the service in case the next service is not available for example. After exceeding the specified maximum of postponements, the job will be considered erroneous.
The key is available for the following services:
-
seal-convert-dispatcher -
seal-controller(deprecated, moved toseal-convert-dispatcheras of PLOSSYS 5.4.0) -
seal-dispatcher(deprecated, replaced byseal-controlleras of PLOSSYS 5.3.0)
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/convert-dispatcher/tag/any/JOB_MAX_POSTPONED_COUNT -
dc/home/env/service/controller/tag/any/JOB_MAX_POSTPONED_COUNT(deprecated, moved toseal-convert-dispatcheras of PLOSSYS 5.4.0) -
dc/home/env/service/dispatcher/tag/any/JOB_MAX_POSTPONED_COUNT(deprecated, replaced byseal-controlleras of PLOSSYS 5.3.0)
Available values: Integer
-
<number_max_postpone>The maximum number of times a job will be postponed.
Default: 10
Hint - printer-specific
As of PLOSSYS 5.3.0, the maximum of postponements can be specified for each printer. For more information, refer to the jobMaxPostponedCount printer key.
JOB_RETRY_DELAY¶
JOB_RETRY_DELAY specifies the waiting time between the postponements in case the next service is not available for example. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-controller service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/controller/tag/any/JOB_RETRY_DELAY
Available values: string
<time_interval_and_unit>
Default: 5s
Hint - new service and key
As of PLOSSYS 5.3.0, the seal-dispatcher service has been replaced by the seal-controller service and the previous key LOUNGE_TTL has been replaced by JOB_RETRY_DELAY.
JOBS_METADATA¶
JOBS_METADATA specifies the job properties to be displayed as additional columns in the job view of the PLOSSYS Administrator. For more information about the configuration, refer to Configure Additional Columns.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/JOBS_METADATA
Available values: String
<json_array_with_job_parameters>
Default: [{}]
Each property is specified using the following keys:
-
name: Internal name of the property; the name has to be unique. -
path: Any property within your job object; for an example of a job's database object, refer to Example of a Job's Database Object. -
type: Type of the column; available values aretext,number,timestampandlink. -
view: Is the column visible when the application is started for the first time; available values areextended(not visible) andstandard(visible). -
searchable: Is the user allowed to search for values in the column? Available values aretrueandfalse.
Example - add columns for the arrival time and the checkin type
[
{
"name": "arrivedTime",
"path": "orig.arrivedTime",
"type": "timestamp",
"view": "extended",
"searchable": "false"
},
{
"name": "checkinType",
"path": "orig.checkinType",
"type": "text",
"view": "extended",
"searchable": "true"
}
]
Example - show DDD job names for PDE
[
{
"name": "arrivedTime",
"path": "current.arrivedTime",
"type": "timestamp",
"view": "extended",
"searchable": "false"
},
{
"name": "checkinType",
"path": "orig.checkinType",
"type": "text",
"view": "extended",
"searchable": "true"
},
{
"name": "PRINTJOB_NUMBER",
"path": "current.PRINTJOB_NUMBER",
"type": "text",
"view": "standard",
"searchable": "true"
},
{
"name": "PRINTJOB_TYPE",
"path": "current.PRINTJOB_TYPE",
"type": "text",
"view": "standard",
"searchable": "true"
},
{
"name": "SAPBO_OBJECTKEY",
"path": "current.SAPBO_OBJECTKEY",
"type": "text",
"view": "standard",
"searchable": "true"
},
{
"name": "SAPBO_OBJECTTYPE",
"path": "current.SAPBO_OBJECTTYPE",
"type": "text",
"view": "standard",
"searchable": "true"
}
]
JWT_ROLES¶
JWT_ROLES specifies the property name set in the JSON Web Token (JWT) for accessing the user roles.
The key is available for the seal-rest service.
In Consul, the key is specified here:
dc/home/env/service/rest/tag/any/JWT_ROLES
Available values: String
<property_name>
Default: none
JWT_USERNAME¶
JWT_USERNAME specifies the property name set in the JSON Web Token (JWT) for accessing the user name. The user name is used for audit data only.
The key is available for the seal-rest service.
In Consul, the key is specified here:
dc/home/env/service/rest/tag/any/JWT_USERNAME
Available values: String
<property_name>
Default: sub
KIBANA_INDEX_PATTERN_LOG¶
KIBANA_INDEX_PATTERN_LOG specifies the index pattern where the log data is stored in Elasticsearch.
The key is available for the following services:
seal-plossysadmin
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/KIBANA_INDEX_PATTERN_LOG
Available values: String
<index_name>
Default: seal-plossys-5-log
KIBANA_JOB_METADATA¶
KIBANA_JOB_METADATA specifies the job metadata used in KIBANA_LINK. The columns corresponding to the metadata are displayed in the order of the comma-separated list.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/KIBANA_JOB_METADATA
Available values: String
<comma_separated_list>
Default: message,metadata.jobId,level,metadata.jobName
KIBANA_LINK¶
KIBANA_LINK specifies the URL under which the Kibana app is available.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/KIBANA_LINK
Available values: String
<url_kibana_app>
Default: http://localhost:5601/app/kibana
KIBANA_PRINTER_METADATA¶
KIBANA_PRINTER_METADATA specifies the printer metadata used in KIBANA_LINK. The columns corresponding to the metadata are displayed in the order of the comma-separated list.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/KIBANA_PRINTER_METADATA
Available values: String
<comma_separated_list>
Default: message,metadata.printer,level
LAST_PAGE_SAVE_INTERVAL¶
LAST_PAGE_SAVE_INTERVAL specifies the number of pages after which the number of output pages is written to the database regularly.This key is only valid for PJL printers (pjl protocol), refer to Use PJL Output.
The key is available for the seal-pjl-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/pjl-checkout/tag/any/LAST_PAGE_SAVE_INTERVAL
Available values: Integer
<number_of_pages>
Default: 0 (= off)
LOG_FULL_JOB_PROPERTIES¶
LOG_FULL_JOB_PROPERTIES specifies if all metadata fields of a job are logged. The correspondent log message begins with Job metadata.
The key is available for the following services:
-
seal-checkin -
seal-ipp-checkin
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/checkin/tag/lpr/LOG_FULL_JOB_PROPERTIES -
dc/home/env/service/checkin/tag/ipp/LOG_FULL_JOB_PROPERTIES
Available values: String
-
YThe metadata fields of a job are logged.
-
NThe metadata fields of a job are not logged.
Default: N
LOG_LEVEL¶
LOG_LEVEL specifies the log level for the correspondent service. Messages that correspond to this log level or a higher one are written to the log file.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/any/tag/any/LOG_LEVELfor all services -
dc/home/env/service/<service>/tag/any/LOG_LEVELfor the specific<service>service
Available values: String
-
debugDebug messages are written to the log file of the service.
-
infoInformation messages are written to the log file of the service.
-
warnWarning messages are written to the log file of the service.
-
errorError messages are written to the log file of the service.
-
fatalSerious error messages are written to the log file of the service.
Default: info
Example - log level error
Messages of the log levels error and fatal are written to the log file.
Example - log level info
Messages of the log levels info, warn, error and fatal are written to the log file.
LOUNGE_TTL¶
LOUNGE_TTL specifies the time interval between two transmission attempts in case of error. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the following services:
-
seal-convert-dispatcher -
seal-dispatcher(deprecated)
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/convert-dispatcher/tag/any/LOUNGE_TTL -
dc/home/env/service/dispatcher/tag/any/LOUNGE_TTL(deprecated)
Available values: String
<time_interval_and_unit>
Default: 1m
LPR_ENCODING¶
LPR_ENCODING specifies the encoding of the job that is accepted or output via LPR.
The key is available for the following services:
-
seal-checkin -
seal-checkout -
seal-mainland-checkout
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/checkin/tag/lpr/LPR_ENCODING -
dc/home/env/service/checkout/tag/any/LPR_ENCODING -
dc/home/env/service/anymainland-checkout/tag/any/LPR_ENCODING
Available values: String
Default: win1252
MAX_INSTANCES¶
MAX_INSTANCES specifies the maximum of parallel conversions.
The key is available for the following services:
-
seal-convert-pdf2ps -
seal-convert-ps2pdf -
seal-convert-sapgof -
seal-ghost
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/convert-pdf2ps/tag/any/MAX_INSTANCES -
dc/home/env/service/convert-ps2pdf/tag/any/MAX_INSTANCES -
dc/home/env/service/convert-sapgof/tag/any/MAX_INSTANCES -
dc/home/env/service/ghost/tag/any/MAX_INSTANCES
Available values: Integer
<number_instances>
Default: Number of the available CPU cores in the system
METRIC_INTERVAL¶
METRIC_INTERVAL specifies the time interval after which the metrics are written to the log. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the following services:
seal-ipp-checkin
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/checkin/tag/ipp/METRIC_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 0s
MONGO_CONFIGS_URL¶
MONGO_CONFIGS_URL specifies the URL of the database where the user-specific settings of PLOSSYS Administrator are stored centrally so that they apply to all browsers. In case of a cluster, all URLs and the configured replica set have to be specified. If the port is not specified, the default port 27017 is used.
The key is available for the seal-rest service.
In Consul, the key is specified here:
dc/home/env/service/rest/tag/any/MONGO_CONFIGS_URL
Available values: String
-
mongodb://<server>:<port>/spooler-configsfor a single MongoDB server -
mongodb://<server1>,<server2>,<server3>:<port>/spooler-configs?replicaSet=<replica_set>for MongoDB in cluster mode
Default: mongodb://localhost:27017/spooler-configs
MONGO_CONNECT_RETRIES¶
MONGO_CONNECT_RETRIES specifies the number of attempts of a service to connect to the database.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/MONGO_CONNECT_RETRIES
Available values: Integer
<number_retries>
Default: 10
MONGO_EVENTS_COLLECTION_SIZE¶
MONGO_EVENTS_COLLECTION_SIZE specifies the size of the capped collection used to store events in the database.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/MONGO_EVENTS_COLLECTION_SIZE
Available values: String
<collection_size>
Default: 1MB
MONGO_EVENTS_URL¶
MONGO_EVENTS_URL specifies the URL of the database where the internal system notifications are stored. In case of a cluster, all URLs and the configured replica set have to be specified. If the port is not specified, the default port 27017 is used.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/MONGO_EVENTS_URL
Available values: String
-
mongodb://<server>:<port>/spooler-eventsfor a single MongoDB server -
mongodb://<server1>,<server2>,<server3>:<port>/spooler-events?replicaSet=<replica_set>for MongoDB in cluster mode
Default: mongodb://localhost:27017/spooler-events
MONGO_JOBS_URL¶
MONGO_JOBS_URL specifies the URL of the database where the job data is stored. In case of a cluster, all URLs and the configured replica set have to be specified. If the port is not specified, the default port 27017 is used.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/MONGO_JOBS_URL
Available values: String
-
mongodb://<server>:<port>/spooler-jobsfor a single MongoDB server -
mongodb://<server1>,<server2>,<server3>:<port>/spooler-jobs?replicaSet=<replica_set>for MongoDB in cluster mode
Default: mongodb://localhost:27017/spooler-jobs
MONGO_LOCKER_POOL_SIZE¶
MONGO_LOCKER_POOL_SIZE specifies the maximum number of parallel database connections per process for accessing locks and actions.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/MONGO_LOCKER_POOL_SIZE
Available values: Integer
<number_max_pool_size>
Default: 20
MONGO_LOCKS_AGE¶
MONGO_LOCKS_AGE specifies the time interval after which a lock is regarded as outdated and deleted from the database. A quarter of MONGO_LOCKS_AGE is used as lock-update interval by all services. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/all/tag/any/MONGO_LOCKS_AGE
Available values: String
<time_interval_and_unit>
Default: 1m
MONGO_LOCKS_URL¶
MONGO_LOCKS_URL specifies the URL of the database where the data for the system-wide locking is stored. In case of a cluster, all URLs and the configured replica set have to be specified. If the port is not specified, the default port 27017 is used.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/MONGO_LOCKS_URL
Available values: String
-
mongodb://<server>:<port>/spooler-locksfor a single MongoDB server -
mongodb://<server1>,<server2>,<server3>:<port>/spooler-locks?replicaSet=<replica_set>for MongoDB in cluster mode
Default: mongodb://localhost:27017/spooler-locks
MONGO_LOCKS_INTERVAL¶
MONGO_LOCKS_INTERVAL specifies the time interval after which the ages of the locks are checked. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/MONGO_LOCKS_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 5s
MONGO_NOTIFICATIONS_URL¶
MONGO_NOTIFICATIONS_URL specifies the URL of the database where the seal-co-notifier service stores its private data. In case of a cluster, all URLs and the configured replica set have to be specified. If the port is not specified, the default port 27017 is used.
The key is available for the seal-co-notifier service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/co-notifier/tag/any/MONGO_NOTIFICATIONS_URL
Available values: String
-
mongodb://<server>:<port>/spooler-notificationsfor a single MongoDB server -
mongodb://<server1>,<server2>,<server3>:<port>/spooler-notifications?replicaSet=<replica_set>for MongoDB in cluster mode
Default: mongodb://localhost:27017/spooler-notifications
MONGO_PREPROCESS_URL¶
MONGO_PREPROCESS_URL specifies the URL of the database where the flow configuration for the preprocessing is stored. In case of a cluster, all URLs and the configured replica set have to be specified. If the port is not specified, the default port 27017 is used.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/MONGO_PPREPROCESS_URL
Available values: String
-
mongodb://<server>:<port>/spooler-preprocessfor a single MongoDB server -
mongodb://<server1>,<server2>,<server3>:<port>/spooler-preprocess?replicaSet=<replica_set>for MongoDB in cluster mode
Default: mongodb://localhost:27017/spooler-preprocess
MONGO_PRINTERS_URL¶
MONGO_PRINTERS_URL specifies the URL of the database where the printer configuration is stored. In case of a cluster, all URLs and the configured replica set have to be specified. If the port is not specified, the default port 27017 is used.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/MONGO_PRINTERS_URL
Available values: String
-
mongodb://<server>:<port>/spooler-printersfor a single MongoDB server -
mongodb://<server1>,<server2>,<server3>:<port>/spooler-printers?replicaSet=<replica_set>for MongoDB in cluster mode
Default: mongodb://localhost:27017/spooler-printers
MONGO_REMOTE_SITES_URL¶
MONGO_REMOTE_SITES_URL specifies the URL of the database where the island-checkout connections are stored. In case of a cluster, all URLs and the configured replica set have to be specified. If the port is not specified, the default port 27017 is used.
The key is available for the seal-mainland-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/mainland-checkout/tag/any/MONGO_REMOTE_SITES_URL
Available values: String
-
mongodb://<server>:<port>/spooler-remote-sitesfor a single MongoDB server -
mongodb://<server1>,<server2>,<server3>:<port>/spooler-remote-sites?replicaSet=<replica_set>for MongoDB in cluster mode
Default: mongodb://localhost:27017/spooler-remote-sites
MONGODB_FORCE_TLS¶
MONGODB_FORCE_TLS specifies if connections to the MongoDB database uses always TLS. The existence of the key is sufficient to enforce TLS.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/MONGODB_FORCE_TLS
Available values: any
Default: Depends on the value of TLS_UNPROTECTED
NODE_TLS_REJECT_UNAUTHORIZED¶
NODE_TLS_REJECT_UNAUTHORIZED specifies if self-signed certificates are allowed.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/NODE_TLS_REJECT_UNAUTHORIZED
Available values: Integer
-
0Self-signed certificates are allowed.
-
1Self-signed certificates are not allowed.
Default: 1
Caution - security gap
Setting NODE_TLS_REJECT_UNAUTHORIZED to 0 in a productive system is a serious security gap! Only use it for test purposes!
Hint - certificate
Unless NODE_TLS_REJECT_UNAUTHORIZED is set to 0 or specified at all, the certificate has to contain the correct IP address or hostname since this is used for the authorization check.
NOTIFICATION_CALLBACKS¶
NOTIFICATION_CALLBACKS specifies callback actions for particular events like job status updates.
The key is available for the seal-co-notifier service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/co-notifier/tag/any/NOTIFICATION_CALLBACKS
Available values: JSON string format
Default: none
Available message types:
UPDATE_JOB
Available action parameters:
-
action: stringMandatory, contains the callback URI. If the specified protocoll is a valid URL protocoll like
httporhttps, the specified callback URI will be taken as a URL and aPOSTrequest will be generated per default. If another HTTP request method likeGET,PUTorPATCHshould be used instead, themethodparameter has to be set as well. The notification message will be sent as request body (as long as the request method is notGET). -
entireItem: booleanfalseDefault. Only essential object data (likejobId,jobName,userName) and changed object data (status) will be sent.trueThe entire object (job) will be sent. -
key: stringA specific parameter key that has to be contained in the message, f.e.
status. Only in combination with thevalueparameter. -
value: stringSpecific parameter value, that has to be set as value for the specified
keyparameter. Can be a regular expression, f.e..*p402.*. -
method: stringHTTP request method to be used, default:
POST. -
headers: JSON objectOptional HTTP headers to be sent with the request.
The parameters action, value and headers entries can contain placeholders that will be replaced by the corresponding values of the job object.
Example - different callback actions for the event type UPDATE_JOB
{
"UPDATE_JOB": [
{
"method": "GET",
"action": "https://external.web.site.com/update?status={{ status }}&jobId={{ _id }}&userId={{ userName }}"
},
{
"key": "status",
"value": "error",
"action": "http://external.web.site.com/error",
"entireItem": true
},
{
"action": "http://external.web.site.com/headers",
"headers":
{
"My-Header1": "status is in My-Header2",
"My-Header2": "{{ status }}"
}
}
]
}
Literature - use case description
For further information and examples, refer to the use case description Create Callback Actions.
NOTIFICATION_LIFETIME_IPP¶
NOTIFICATION_LIFETIME_IPP specifies the time interval after which a job notification of type IPP is deleted by the seal-housekeeper service from the database. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/NOTIFICATION_LIFETIME_IPP
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: 3d
NOTIFICATION_LIFETIME_SAP¶
NOTIFICATION_LIFETIME_SAP specifies the time interval after which a job notification of type SAP is deleted by the seal-housekeeper service from the database. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page. The time of the actual deletion depends also on the value specified in HOUSEKEEPER_INTERVAL.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/NOTIFICATION_LIFETIME_SAP
Available values: String
-
<time_interval_and_unit> -
-1The time interval will never be reached and so the jobs never will be deleted.
Default: 3d
ORPHAN_CHECK_INTERVAL¶
ORPHAN_CHECK_INTERVAL specifies the time interval between two checks for printers no longer locked by a seal-controller instance. During processing, the printers are locked by a seal-controller instance. If this instance crashes, the lock will be removed by seal-housekeeper after a while. This unlocked printer is than detected not later than the time interval specified with ORPHAN_CHECK_INTERVAL and a new seal-controller instance will lock the printer. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-controller service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/controller/tag/any/ORPHAN_CHECK_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 1m
PAGE_FAILOVER¶
PAGE_FAILOVER specifies if an interrupted job is repeated starting at the page printed last or at the first page. This key is only valid for PJL printers (pjl protocol), refer to Use PJL Output.
The key is available for the seal-pjl-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/pjl-checkout/tag/any/PAGE_FAILOVER
Available values: Boolean
-
trueThe job is repeated starting at the page printed last.
-
falseThe job is repeated starting at the first page.
Default: true
PAGINATION_STEPS¶
PAGINATION_STEPS specifies the selection provided for the number of items to be listed in one page.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/PAGINATION_STEPS
Available values: Comma-separated list of Integers
<no_1>, <no_2>, <no_3> ... <no_n>
Default: 3, 10, 20, 30, 50, 500
Caution - performance
Be aware that high values (> 100) can have a negative influence to the performance!
PAGINATION_DEFAULT_STEP¶
PAGINATION_DEFAULT_STEP specifies the default of the selection for the number of items to be listed in one page. The default has to be one of the values specified with PAGINATION_STEPS.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/PAGINATION_DEFAULT_STEP
Available values: Integer
Default: 20
PACER_INTERVAL¶
PACER_INTERVAL specifies the time interval after which the database is searched again for jobs that have not yet been processed. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the following services:
-
seal-convert-dispatcher -
seal-dispatcher(deprecated)
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/convert-dispatcher/tag/any/PACER_INTERVAL -
dc/home/env/service/dispatcher/tag/any/PACER_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 5m
PAUSE_AFTER_PRINT¶
PAUSE_AFTER_PRINT specifies a pause in milliseconds after each print job.
The key is available for the seal-pjl-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/pjl-checkout/tag/any/PAUSE_AFTER_PRINT
Available values: Integer
<pause in msec>
Default: 0 (= off)
Hint - remote printers
This key has no effect for pjl printers at a remote site.
PICKUP_BLOCK_INACTIVITY_TIMEOUT¶
PICKUP_BLOCK_INACTIVITY_TIMEOUT specifies an additional inactivity timeout after processing one or more pickup jobs released by a user via IPP. The time has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-controller service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/controller/tag/any/PICKUP_BLOCK_INACTIVITY_TIMEOUT
Available values: String
<time_and_unit>
Default: 1m
Example - PICKUP_BLOCK_INACTIVITY_TIMEOUT=1m
- The
released-pickup-job1job's processing took 30 seconds. - The
released-pickup-job2job's processing took 20 seconds. - The inactivity timer kicks in and, after 1 minute 50 seconds, releases the printer again.
- If the
released-pickup-job3job is released earlier before reaching the timeout, the timer will be restarted after the released-pickup-job3 job reached one of the valid end statuses, for example,processedorerror.
POLLING_INTERVAL¶
POLLING_INTERVAL specifies the time interval after which the seal-out-ngn-message-relay service checks for new notifications. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-out-ngn-message-relay service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossys-message-relay/tag/any/POLLING_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 3s
POSTSCRIPT_LEVEL¶
POSTSCRIPT_LEVEL specifies the default postscript level that the PDF to PostScript converter is supposed to generate.
The key is available for the seal-convert-pdf2ps service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/convert-pdf2ps/tag/any/POSTSCRIPT_LEVEL
Available values: Integer
<level>
Default: 3
Hint - printer templates
The postscript level specified in the printer configuration file overwrites this environment key, for example:
pdl:
name: postscript
version: '3.0'
PREVIEW_FORMAT¶
PREVIEW_FORMAT specifies the format used for generating the job previews. The previews are stored in the database and can be displayed in PLOSSYS Administrator for example.
The key is available for the seal-print-preview and the seal-plossysadmin services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/PREVIEW_FORMAT
Available values: String
-
image/jpegThe job previews are generated as JPEG files.
-
application/pdfThe job previews are generated as PDF files.
Default: application/pdf
PRINT_ERROR_SHEET¶
PRINT_ERROR_SHEET specifies if an error sheet is output in case of error.
The key is available for the following services:
-
seal-dispatcher(deprecated) -
seal-convert-dispatcher
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/convert-dispatcher/tag/any/PRINT_ERROR_SHEET -
dc/home/env/service/dispatcher/tag/any/PRINT_ERROR_SHEET(deprecated)
Available values: String
-
YAn error sheet is output in case of error.
-
NNo error sheet is output in case of error.
Default: N
Hint - changes and known bugs
-
Up to version 5.0.5, an error sheet was output in case of error. As of version 5.1.0, the error sheet is not output by default but can be activated by setting
PRINT_ERROR_SHEETtoY. -
With version 5.3.0,
PRINT_ERROR_SHEETdoes not work. -
With version 5.3.2, the service evaluating
PRINT_ERROR_SHEETchanged from theseal-dispatcherto theseal-convert-dispatcherservice.
PRINT_PARAMS¶
PRINT_PARAMS specifies if seal-convert-ps2pdf should read the print parameters like page size or duplex from the postscript document. |
The key is available for the following services:
seal-convert-ps2pdf
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/convert-ps2pdf/tag/any/PRINT_PARAMS
Available values: Boolean
true-
YThe print parameters are read from the postscript document.
-
false -
NThe print parameters are not read from the postscript document.
Default: true
Literature - supported Ghostscript commands
For a list of evaluated parameters, refer to Supported Ghostscript Commands.
PRINTER_CACHE_TTL¶
PRINTER_CACHE_TTL specifies the time interval after that a cached printer object expires.
The key is available for the following services:
-
seal-checkin -
seal-ipp-checkin
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/checkin/tag/lpr/PRINTER_CACHE_TTL -
dc/home/env/service/checkin/tag/ipp/PRINTER_CACHE_TTL
Available values: String
<time_interval_and_unit>
Default: 5m
PRINTER_MONITOR_MODE¶
PRINTER_MONITOR_MODE specifies if and when the physical statuses of the printers are checked. The value can be overwritten for each printer by the printer configuration key monitorMode.
The key is available for the seal-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/checkout/tag/any/PRINTER_MONITOR_MODE
Available values: String
-
AFTER_PRINTCheck the status after printing a job
-
NEVERNever check the status
Default: NEVER
PRINTER_PAGE_RESPONSE_TIMEOUT¶
PRINTER_PAGE_RESPONSE_TIMEOUT specifies the time interval after which the connection to the printer is closed when the printer does not reply messages about the number of printed pages. This key is only valid for PJL printers (pjl protocol), refer to Use PJL Output. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-pjl-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/pjl-checkout/tag/any/PRINTER_PAGE_RESPONSE_TIMEOUT
Available values: String
<time_interval_and_unit>
Default: none
PRINTER_RESPONSE_TIMEOUT¶
PRINTER_RESPONSE_TIMEOUT specifies the time interval after which the connection to the printer is closed when the printer does not reply any message. This key is only valid for PJL printers (pjl protocol), refer to Use PJL Output. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-pjl-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/pjl-checkout/tag/any/PRINTER_RESPONSE_TIMEOUT
Available values: String
<time_interval_and_unit>
Default: 1m
PRINTERS_METADATA¶
PRINTERS_METADATA specifies the printer properties to be displayed as additional columns in the printer view. For more information about the configuration, refer to Configure Additional Columns.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/PRINTERS_METADATA
Available values: String
<json_array_with_printer_parameters>
Default: [{}]
Each property is specified using the following properties:
-
name: Internal name of the property; the name has to be unique. -
path: Any property within your printer object; for an example of a printer's database object, refer to Example of a Printer's Database Object. -
type: Type of the column; available values aretext,number,timestampandlink. -
view: Is the column visible when the application is started for the first time; available values areextended(not visible) andstandard(visible). -
searchable: Is the user allowed to search for values in the column? Available values aretrueandfalse.
Example - add columns for printer manufacturer and the model filters
[
{
"name": "manufacturer",
"path": "config.type.manufacturer",
"type": "text",
"view": "standard",
"searchable": "true"
},
{
"name": "model",
"path": "config.type.model",
"type": "text",
"view": "extended",
"searchable": "true"
}
]
PRINTER_NOTE_ACTION_CONFIRMATION¶
PRINTER_NOTE_ACTION_CONFIRMATION specifies if a confirmation dialog is opened with actions on printers for which notes exist.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/PRINTER_NOTE_ACTION_CONFIRMATION
Available values: String
-
YA confirmation dialog is opened.
-
NNo confirmation dialog is opened.
Default: Y
REST_BASE_URL¶
REST_BASE_URL specifies the address of the PLOSSYS REST API.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/REST_BASE_URL
Available values: String
<rest_url>
Default: https://localhost:8080
REST_VERSION¶
REST_VERSION specifies the version of the URL suffix of the PLOSSYS REST API.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/REST_VERSION
Available values: String
<version>
Default: v3
RFC_TRACE_DIR¶
RFC_TRACE_DIR specifies the directory for the dev_rfc<n>.log files. These files can be created in case of a communication error with SAP.
The key is available for the seal-co-notifier service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/co-notifier/tag/any/RFC_TRACE_DIR
Available values: String
<path>
Default:
-
Windows:
C:\ProgramData\SEAL Systems\log -
Linux:
/var/log/seal/
Hint - priorities
If an environment variable has been set at the host, it will be used instead of the default. If the key is set in Consul, it will have the highest priority.
Caution - Logrotate
SEAL Logrotate will only clean up the dev_rfc<n>.log files if they are in the default directories.
SAP_JOBNOTIFY_TIMEOUT¶
SAP_JOBNOTIFY_TIMEOUT specifies the timeout for sending job notifications to SAP. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-co-notifier service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/co-notifier/tag/any/SAP_JOBNOTIFY_TIMEOUT
Available values: String
<path>
Default: 60s
SAPNWRFCINI_PATH¶
SAPNWRFCINI_PATH specifies the directory where the SAP configuration file sapnwrfc.ini is stored. The key has to be set if notifications are to be returned to the requesting SAP Systems.
The key is available for the seal-co-notifier service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/co-notifier/tag/any/SAPNWRFCINI_PATH
Available values: String
<path>
Default:
-
Windows:
C:/ProgramData/SEAL Systems/PLOSSYS/config -
Linux:
/opt/seal/etc
SERVICE_DISCOVERY¶
SERVICE_DISCOVERY specifies if PLOSSYS Output Engine is running in an on-premise installation or in a cloud environment. In the cloud environment, the configuration is not read from Consul but from files or the environment.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/SERVICE_DISCOVERY
Available values: String
-
cloudPLOSSYS Output Engine is running in a cloud environment.
-
consulPLOSSYS Output Engine is running in an on-premise installation.
Default: consul
SERVICE_URL¶
SERVICE_URL specifies how a service can be accessed.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/checkin/tag/ipp/SERVICE_URLfor theseal-ipp-checkinservicedc/home/env/service/checkin/tag/lpr/SERVICE_URLfor theseal-checkinservicedc/home/env/service/<service>/tag/any/SERVICE_URLfor the other services
Available values: String
<service_url>
Default: The server name is determined when a service is started and the default port is used. The correspondent assignment is described in Used Ports.
Hint - additional configuration with the seal-ipp-checkin service
For enabling both IPP and IPPS communication for the seal-ipp-checkin service, two URLs can be specified with SERVICE_URL.
Example - both IPP and IPPS with the seal-ipp-checkin service
SERVICE_URL: 'ipp://:631 ipps://:632'
SOCKET_CLOSE_TIMEOUT¶
SOCKET_CLOSE_TIMEOUT specifies the timeout after which the socket is forced closed after sending a spool file to the printer unless the printer closes the connection. The time interval has to be specified as the number of milliseconds to wait. For disabling the forced closing, specify 0.
The key is available for the seal-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/checkout/tag/any/SOCKET_CLOSE_TIMEOUT
Available values: Integer
<time_interval>
Default: 0
SOCKET_CLOSE_TIMEOUT_IS_JOB_ERROR¶
SOCKET_CLOSE_TIMEOUT_IS_JOB_ERROR specifies if the job status is set to error after the socket has been forced closed.
The key is available for the seal-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/checkout/tag/any/SOCKET_CLOSE_TIMEOUT_IS_JOB_ERROR
Available values: Boolean
-
trueThe job status is set to error after the socket has been forced closed.
-
falseThe job status is not set to error after the socket has been forced closed.
Default: false
SOCKET_CONNECT_TIMEOUT¶
SOCKET_CONNECT_TIMEOUT specifies the timeout in milliseconds after which a socket connect is aborted.
The key is available for the seal-pjl-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/pjl-checkout/tag/any/SOCKET_CONNECT_TIMEOUT
Available values: Integer
<time_interval>
Default: 60000
SOCKET_TIMEOUT¶
SOCKET_TIMEOUT specifies the socket timeout in milliseconds.
The key is available for the seal-pjl-checkout and the socket output of the seal-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/checkout/tag/any/SOCKET_TIMEOUTdc/home/env/service/pjl-checkout/tag/any/SOCKET_TIMEOUT
Available values: Integer
<time_interval>
Default: 300000
SWEEP_AGE¶
SWEEP_AGE specifies the time interval after which an incomplete job is regarded as incorrect and deleted from the database. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-housekeeper service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/housekeeper/tag/any/SWEEP_AGE
Available values: String
<time_interval_and_unit>
Default: Maximum of all other JOB_LIFETIME_* values for the seal-housekeeper service; default is 3d.
SYSTEMS¶
SYSTEMS specifies the list of SAP systems whose output jobs are to be stamped. The value is a multiline text containing one system name in each line.
The key is available for the seal-convert-dispatcher service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/plossys/sapgof/stamp/SYSTEMS
Available values: Multiline string
-
<system1><system2>...<systemn>
Default: none
Example
Hint - syntax
The data consists of multiple lines. When entering the data as YAML, store the value in literal style for preserving the line endings, indicated by a |. You have to indent all lines of the text. The leading spaces will not be part of the data retrieved by the service.
TEMPLATE¶
TEMPLATE specifies the content of the stamp layout file for the SAP output jobs.
The key is available for the seal-convert-pdfstamp service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/plossys/sapgof/stamp/TEMPLATE
Available values: String
<template_file_content>
Default: The default layout of PDF Stamp is used, which is contained in the following file:
-
On Windows:
C:\Program Files\SEAL Systems\seal-convert-pdfstamp\lib\config\default.stp -
On Linux:
/opt/seal/seal-convert-pdfstamp/lib/config/default.stp
Literature - PDF Stamp
For more information about PDF Stamp, refer to the PDF Stamp documentation.
TEXT¶
TEMPLATE specifies the stamp text for the SAP output jobs. In the text, variables can be specified.
The key is available for the seal-convert-pdfstamp service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/plossys/sapgof/stamp/TEXT
Available values: String
<stamp_text>
Default: The default text of PDF Stamp is used, which is contained in the following file:
-
On Windows:
C:\Program Files\SEAL Systems\seal-convert-pdfstamp\lib\config\default.txt -
On Linux:
/opt/seal/seal-convert-pdfstamp/lib/config/default.txt
Literature - PDF Stamp
For more information about PDF Stamp, refer to the PDF Stamp documentation.
TIMEOUT¶
TIMEOUT specifies the time interval after which a conversion is aborted if it has not generated any new data. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the following services:
-
seal-convert-pdf2ps -
seal-convert-ps2pdf -
seal-convert-sapgof -
seal-convert-pdfstamp
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/convert-pdf2ps/tag/any/TIMEOUT -
dc/home/env/service/convert-ps2pdf/tag/any/TIMEOUT -
dc/home/env/service/convert-sapgof/tag/any/TIMEOUT -
dc/home/env/service/convert-pdfstamp/tag/any/TIMEOUT
Available values: String
<time_interval_and_unit>
Default: 2m
TLS_CIPHERS¶
TLS_CIPHERS specifies the TLS ciphers, which seal-mainland-checkout will accept when connected from seal-island-checkout. The default is an empty string, which means seal-mainland-checkout will accept all valid TLS ciphers.
The key is available for the seal-mainland-checkout service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/mainland-checkout/tag/any/TLS_CIPHERS
Available values:
- All valid TLS ciphers
Default: ''
TLS_DIR¶
TLS_DIR specifies the directory containing the certificate files necessary for the secure transfer within PLOSSYS Output Engine.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/TLS_DIR
Available values: String
<dir_name>
The directory contains the following files:
-
key.pemFile with the private key
-
cert.pemFile with the certificate
-
ca.pem(optional)File with the CA certificate
Default: none
Hint - certificate files contained in delivery
The self-signed certificates contained in delivery are hard-coded. The tls directories contained in delivery only contain examples which certificate files are required and how they look like.
Hint - tls certificate fallback chain
TLS_EXTERNAL_DIR -> TLS_PADIR -> TLS_DIR -> built-in certificates
TLS_EXTERNAL_DIR¶
TLS_EXTERNAL_DIR specifies the directory containing the external certificate files necessary for the services handling external requests.
The key is available for the following services:
-
seal-plossysadmin -
seal-ipp-checkin -
seal-rest
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/seal-plossysadmin/tag/any/TLS_EXTERNAL_DIR -
dc/home/env/service/seal-ipp-checkin/tag/any/TLS_EXTERNAL_DIR -
dc/home/env/service/seal-rest/tag/any/TLS_EXTERNAL_DIR
Instead of setting the key for each service, it can also be specified here once and for all:
dc/home/env/service/any/tag/any/TLS_EXTERNAL_DIR
Available values: String
<dir_name>
The directory contains the following files:
-
key.pemFile with the private key
-
cert.pemFile with the certificate
-
ca.pem(optional)File with the CA certificate
Default: none
Hint - downward compatibility and fallback
For PLOSSYS Administrator, TLS_EXTERNAL_DIR replaces TLS_PADIR. TLS_PADIR will still work for the time being but should be renamed to TLS_EXTERNAL_DIR.
tls certificate fallback chain:
TLS_EXTERNAL_DIR -> TLS_PADIR -> TLS_DIR -> built-in certificates
TLS_MIN_VERSION¶
TLS_MIN_VERSION specifies the minimum used version of the TLS (Transport Layer Security) encryption protocol between Output Engine services. The services among each other define the highest possible protocol version. Even if TLSv1.2 is set as minimum version, a higher version for the protocol can be negotiated between two services.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/TLS_MIN_VERSION
Available values: String
-
TLSv1.2Use version 1.2 or higher of the TLS protocol.
-
TLSv1.3Version 1.3 of the TLS protocol.
Default: The default is the tls.DEFAULT_MIN_VERSION of the used Node.js version. As of PLOSSYS 5 version 5.7.0, this is TLSv1.2. Older versions than TLSv1.2 are not supported any longer.
Hint - encryption
To activate encryption, set TLS_UNPROTECTED to none.
Hint - TLS_PROTOCOL obsolet
As of PLOSSYS 5.7.0, the environment variable TLS_PROTOCOL is obsolet.
TLS_PADIR¶
TLS_PADIR specifies the directory containing the certificate files necessary for secure transfer with PLOSSYS Administrator.
Caution - use TLS_EXTERNAL_DIR instead
With PLOSSYS version 5.5.1.1085, TLS_PADIR has been replaced by TLS_EXTERNAL_DIR. TLS_PADIR will still work for the time being but should be renamed to TLS_EXTERNAL_DIR.
The key is available for the seal-plossysadmin service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/plossysadmin/tag/any/TLS_PADIR
Available values: String
<dir_name>
The directory contains the following files:
-
key.pemFile with the private key
-
cert.pemFile with the certificate
-
ca.pem(optional)File with the CA certificate
Default: none
Hint - certificate files contained in delivery
The self-signed certificates contained in delivery are hard-coded. The tls directories contained in delivery only contain examples which certificate files are required and how they look like.
Hint - fallback chain
TLS_EXTERNAL_DIR -> TLS_PADIR -> TLS_DIR -> built-in certificates
TLS_UNPROTECTED¶
TLS_UNPROTECTED specifies the encryption between the Output Engine services.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/TLS_UNPROTECTED
Available values: String
-
noneAll connections are encrypted via HTTPS.
-
loopbackThe local connections are not encrypted. The connections between different servers are encrypted via HTTPS.
Default: loopback
USE_ETAG¶
USE_ETAG specifies if the ETag handling is activated or deactivated in the services. In some cases with activated ETag handling, the services returns the HTTP status code 304 (Not Modified) erroneously. By default, the ETag handling is activated in order to reduce data traffic.
The key is available for the following services:
-
seal-rest -
seal-plossysadmin
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
-
dc/home/env/service/rest/tag/any/USE_ETAG -
dc/home/env/service/plossysadmin/tag/any/USE_ETAG
Available values: Boolean
-
YThe ETag handling is activated.
-
NThe ETag handling is deactivated.
Default: Y